From both an economic and a societal point of view, it is essential to consider security and privacy as integral parts of network design from the outset. Additionally, the envisioned security approach must be flexible and sustainable enough to meet the challenges of technological developments which can serve as a basis for future attacks. Therefore, the emerging threat of attacks by quantum computers and quantum hardware must be systematically investigated and defense mechanisms based on post-quantum cryptography and (quantum) physical layer security must be developed. A further focus is on the defense against intrusions as well as on the detection of intrinsic malfunctions and functional conflicts in the network. This calls for a holistic security architecture for 6G networks that follows the paradigm of security-by-design.
One of the most important components for fully securing a system is the use of standardized mechanisms to ensure both safety and security. For example, a clear definition of a rights and role concept in relation to the communication of interfaces and services is urgently required. Furthermore, separation concepts, firewall-friendly designs, minimization of the effects of denial of service and the implementation of a zero-trust model must be considered and solutions integrated. One of the main enhancements in 6G will be Open Radio Access Networks (RANs). The measures mentioned can be applied holistically to the Open RAN system. The problem is that these criteria are often not at the focus of initial development and subsequent implementation work regarding security issues often poses major challenges.
Therefore, we are focusing on:
Once they exist with sufficient power, universal quantum computers will break the currently used public-key cryptography. Since it is to be feared that such powerful quantum computers will exist during the lifespan of the 6G network, from the outset of 6G only cryptography that withstands quantum attackers should be used. While symmetric cryptography can still be used in the era of quantum computers, the current public-key schemes must be replaced by so-called post-quantum cryptography, which cannot be broken even by attackers with access to quantum computers. Compared to classical public-key cryptography, the security of post-quantum schemes relies on more involved hardness assumptions using the mathematics of error-correcting codes, isogenies, lattices, multivariate equations, or constructions using symmetric primitives such as hash functions.
The research topics include:
With the emergence of new networking architectures and services, there has been an increased interest in the potential of information-theoretic approaches to provide communication security by exploiting the physical characteristics of propagation channels. This is the case in MTC for IoT where simple and inexpensive devices are to be deployed, and therefore resource-efficient procedures of low complexity are required. Physical layer security is a promising mechanism to achieve confidentiality by exploiting the inherent randomness of wireless channels at the physical layer, which makes it particularly suitable for implementation in IoT systems, where small payloads, limited computational capabilities and low-latency constraints, make it hard to employ current cryptographic methods. As per requirements on physical layer security, no limitations are imposed on the eavesdroppers in terms of their computational capabilities.
The research topics include:
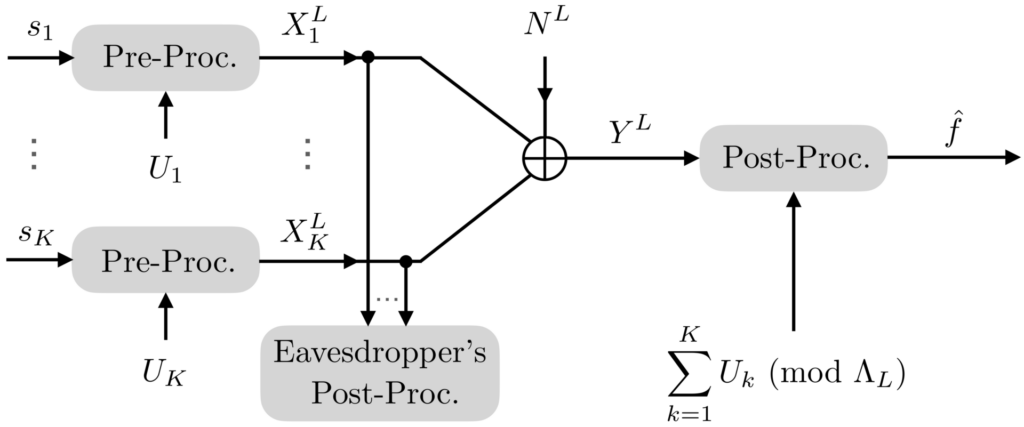
The convergence of sensing and communication as well as envisioned functionalities like in-network computing and machine learning pose serious challenges to privacy, as they heavily rely on distributed processing of private or proprietary data. From a privacy perspective, it is essential to collect only user-related data that is necessary for the operation of the network and, additionally, include proactively privacy-preserving mechanisms in the design of communication protocols. In addition to supplementing existing protocol modules, such as channel charting, with privacy aspects by incorporating differential privacy and/or homomorphic encryption, new methods for analog distributed computation based on methods from lattice coding are also being developed.